CYBER THREAT INTELLIGENCE
Cyber incidents can be identified in a number of different ways. The main challenge here is to gain investigative approaches from information, and to filter out the information that is really relevant from a mass of unstructured data available inside and outside one’s own organisation. rsCyInt is the solution for effective structuring, analysis, classification, visualisation, reporting and joint use of cyber knowledge and intelligence.

Cyber threat analysis
rsCyInt allows analysts to classify cyber attacks, and to describe possible impacts of such attacks based on strong indicators. The objective here is to understand the “nature” of the attack based on its DNA, to identify the attack vector and to propose countermeasures. Comprehensive data sources are available to the experts for this purpose via interfaces. The solution also enables secure data exchange with third parties.
Cyber threat prevention
rsCyInt supports decision-makers in the evaluation of preventive measures for identified threats, and in the definition of appropriate countermeasures. Operative staff subsequently implement these measures to prevent the occurrence of specific cyber threats, either prophylactically or with specific actions based on reliable interpretation.
Cyber threat detection
In terms of both manual and automated mechanisms, rsCyInt offers the experts a vast range of monitoring tools. Not even the most intelligently executed attack may remain undetected. In this context, firewalls alone can never provide 100% protection. Analysis software in combination with learning systems and experienced experts reduces the time advantage of a cyber attack. Digital tripwires based on historical patterns accurately recognise relationships.
Incident response
If a cyber attack has been detected, rapid and prudent action is necessary. rsCyInt guides IT experts logically through each incident. The software searches for patterns of current and historical attacks, and analyses these automatically in terms of the threat assessment.
PROCESS SUPPORT IN THE CASE OF ATTACKS
Cyber threat intelligence is a complex process that uses proven technology to support all of the steps involved in the analysis and management of attacks. rsCyInt provides excellent support for all steps and processes via its single-cockpit solution, based on more than just cyber use cases. rola brings the data models of the cyber world and those of the real world together, and makes full use of its core areas of competence: the provision of intelligence management and analysis solutions for security authorities, the military, and intelligence services.
STIX and MAEC support for a new level of situation overview quality
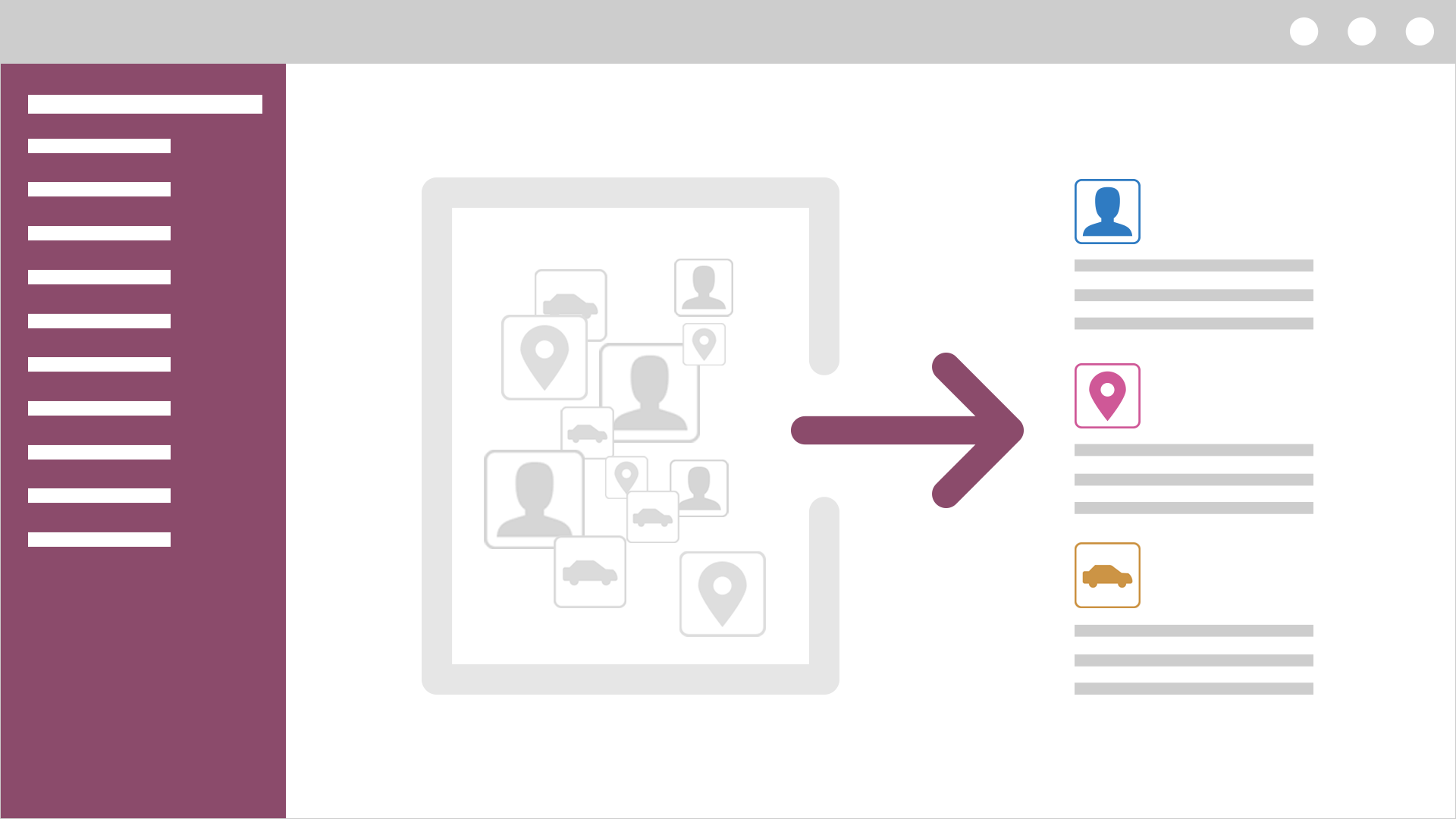
A combination of analysis methods from the real world, for example when searching for vehicles, individual persons, addresses, telephone numbers or movement patterns, and the data models from cyberspace, such as IP addresses, code patterns and hacker groups, results in an enhanced situation overview for the pursuit of perpetrators. This data model mix for the comprehensive analysis is made possible by integration of the STIX (Structured Threat Information eXpression) and MAEC (Malware Attribute Enumeration and Characterisation) data models in rsCyInt.

Interfaces for data fusion
rsCyInt by default includes the interface framework from the rsFrame core, thus enabling multiple data flows from the cyber world and the real world into rsCyInt. In terms of the cyber analysis capability, this means that the STIX model is supported in addition to our other interface capabilities. This enables inclusion of commercial information such as CTI feeds from other sources and platforms. The interface framework can also be used to share information from rsCyInt with external systems, and in this way to, for example, establish a network of experts and organisations for search purposes.

Structuring the unstructured – automatic extraction of entities
A lot of the information that could be of relevance to an investigation or an analysis is still documented and shared in unstructured files. For this reason, rsExtract was created and can be used as a fully integrated module in rsCyInt. In this way, unstructured data can be indexed fully automatically, and objects such as individual persons, company names or IP addresses recognised.
Task management orchestrates the defence
Professional task management is indispensable to enable workflows between multiple teams of experts or to enforce activities. In the case of an acute, global attack, it may be necessary to immediately search for a classified IP address in the log files of one’s own organisation: Already attacked or not? The rsCyInt module has the flexibility to assign tasks and define responsibilities.

ADDITIONAL FUNCTIONS
THE BASIS OF ALL PRODUCTS
As the core element of the solution, rsFrame is always available in the background. Only with this combination of components does the software system exploit its full strengths: not merely the data consolidation but also the direct provision for other systems. The active data exchange and fast analyses are the decisive features.



